- Getting Started
- Recommended Integration & Registration Flow
- Admin Console Overview
- User Onboarding and Management
- User Registration and Login
- Enterprise Applications
- Microsoft Integration
- Installing TraitWare PAM Module for SSH and SFTP
User Sync / LDAP Configuration
Posted on June 4, 2019
Content Navigation
- Customer Settings
- Synchronization Type
- Microsoft Graph API (Hybrid or Cloud Only)
- Azure Active Directory (Hybrid or Cloud Only)
- Microsoft Active Directory (On-Premise Only) or Generic LDAP
- Attribute Mapping
- Self-Signed Certs
- Toggle/Manage Group Sync
- Azure Environment
- Create Azure Cloud User
Admin Console Access
- If you don’t already have an active TraitWare account, Sign up for a fully Automated Free 30-day Trial (Admin Account Level)
- Once you have access to TraitWare, navigate to admin.traitware.com
- Sign in by scanning the QR with your TraitWare app
Customer Settings
- Make sure you are in the TraitWare Customer Console (TCC) (you will see what console you are in in the upper right)
- If you are not in the TCC, choose Select Console Level and select TCC
- If you have more than one customer in your account, select the appropriate name from the dropdown to the right
- Once you are in the appropriate customer account, you will see menu options on the left
- Navigate to User Sync on the left
- You will see the User Synchronization Configuration options
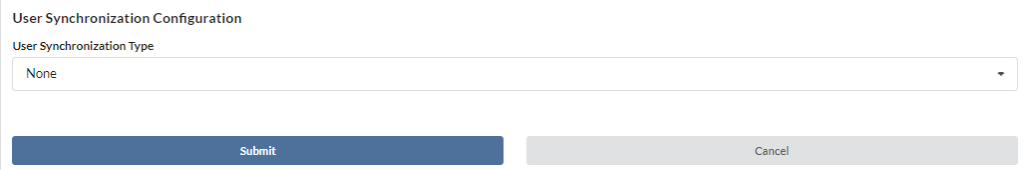
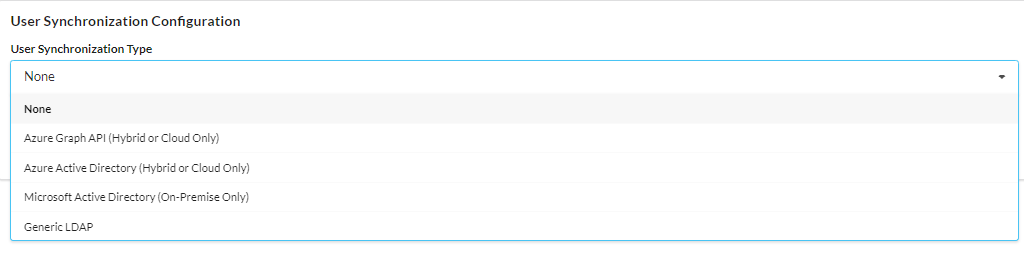
Choose Synchronization Type
- Select the box to choose your User Synchronization Type
- Depending on which one you choose, different options will become available to you
Microsoft Graph API
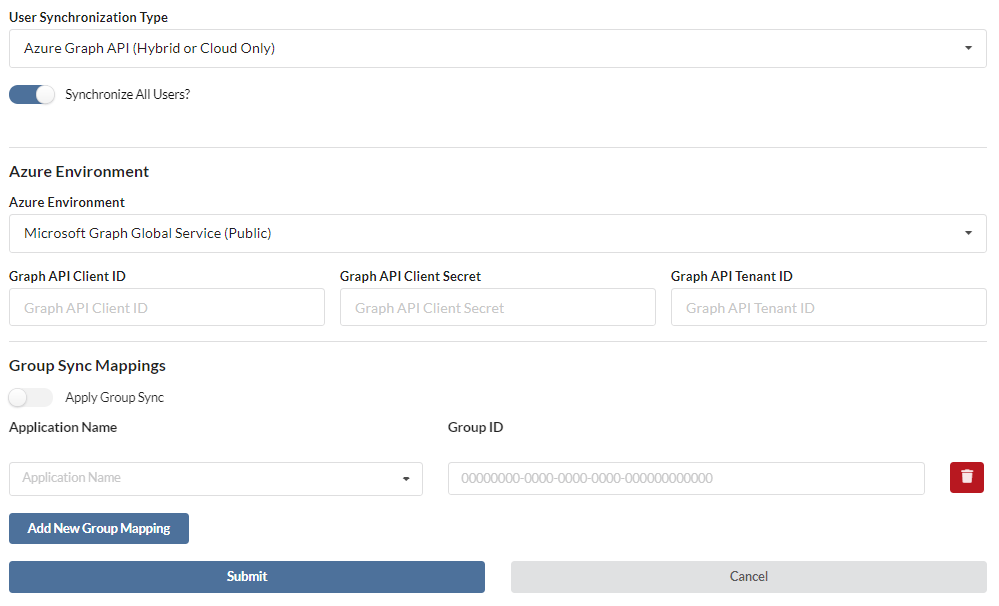
- The Microsoft Graph API sync requires a App registration on Azure using specific TraitWare settings. If you have not already received these, please contact us at support@traitware.com
- You can choose to Synchronize All Users or sync by Azure Group Object Ids
- For details on setting up the Azure Environment, go here
- For details on setting up Group Sync Mappings, go here

Azure Active Directory
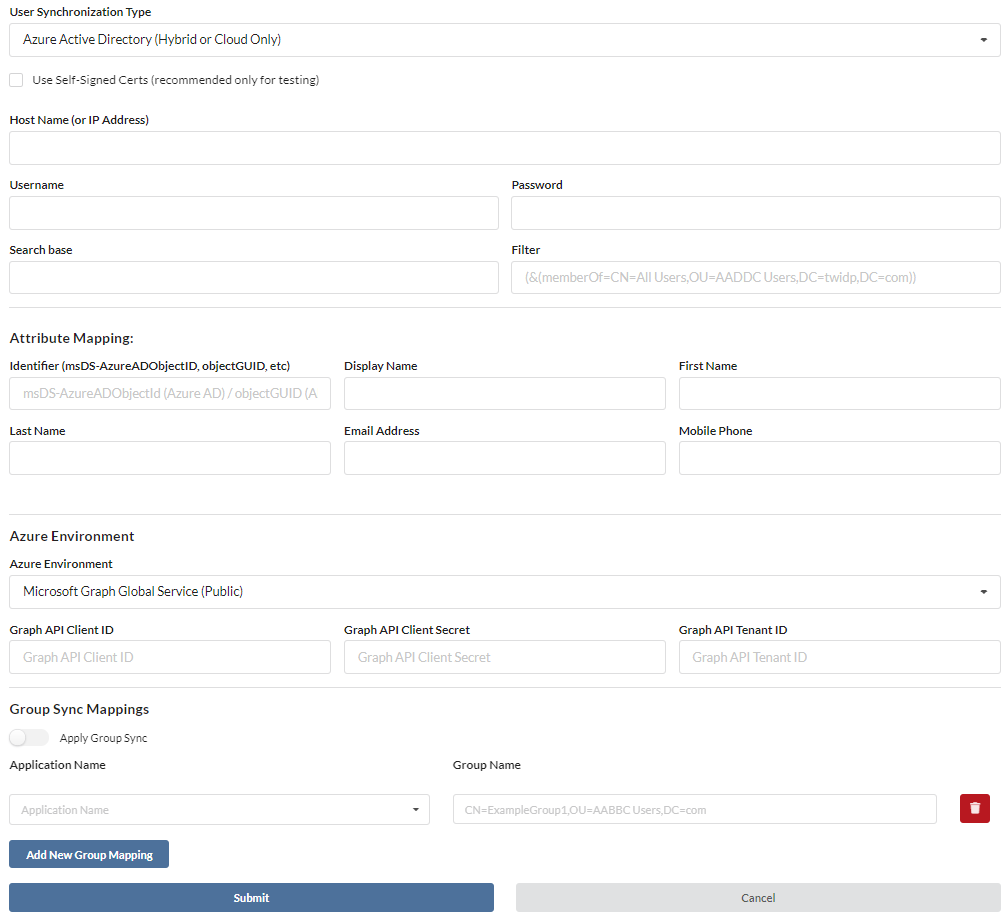
- The Azure Active Directory Sync, you will need to use Azure Active Directory Domain Services (AADS) along with setting up a Graph API in your Azure
- The Host Name should be the domain or IP Address where your LDAP resides
- For Username and Password, use the information for a Global Administrator account which can access the information in your LDAP
- For the Search base, use the information you wish to limit the sync to search. i.e. ou=Users,dc=domain,dc=com
- For Filter, use this information to limit the search within your search base. i.e. (&(memberOf=CN=All Users,OU=Users,DC=domain,DC=com))
- For details on using Self-Signed Certs, go here
- For details on setting up the Attribute Mapping, go here
- For details on setting up the Azure Environment, go here
- For details on setting up Group Sync Mappings, go here
Microsoft Active Directory or Generic LDAP
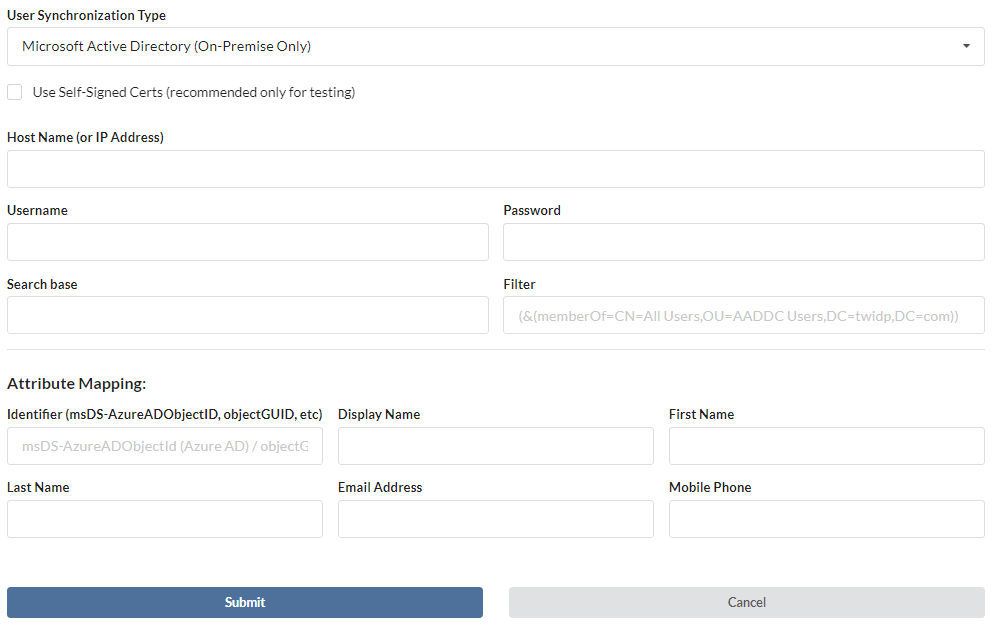
- All of the fields in the upper section are required
- The Host Name should be the domain or IP Address where your LDAP resides
- For Username and Password, use the information for an administrator account which can access the information in your LDAP
- For the Search base, use the information you wish to limit the sync to search. i.e. ou=Users,dc=domain,dc=com
- For Filter, use this information to limit the search within your search base. i.e. (&(memberOf=CN=All Users,OU=Users,DC=domain,DC=com))
- For more on Attribute Mapping, go here
- For more information on Self-Signed Certs, go here
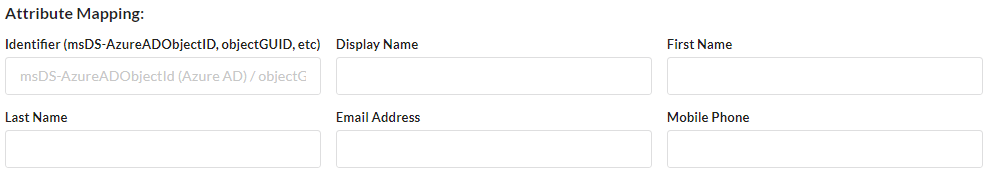
Attribute Mapping
- Attribute Mapping is available for all synchronization types except Microsoft Graph API
- For the Attribute Mapping, you will need to fill in the information so that TraitWare knows what format your users are coming in as
- The Identifier is something to identify the environment it’s coming from
- The Username/Display Name is how the user is displayed in your LDAP
- First Name and Last Name will be something like givenName, surName, or even just sn.
- Email Address, if using Azure sync, will need to be userPrincipalName, otherwise, you can use whatever your LDAP uses
- Mobile Phone is the telephone number field in your LDAP. The fields are not required to have information in them in your LDAP, but an attribute still must be listed, such as telephoneNumber
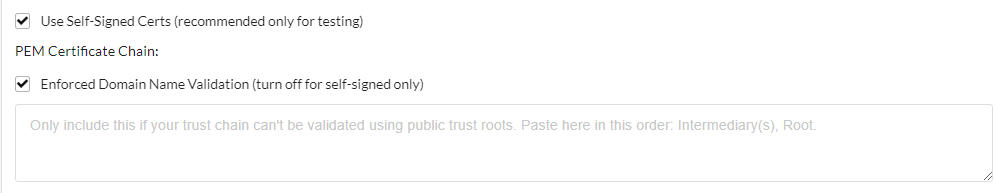
Self-Signed Certs
- Self-Signed Certs are only available when using Azure Active Directory (Hybrid or Cloud), Microsoft Active Directory (On-Premise) or Generic LDAP
- If you have a self-signed certificate for your LDAP, check the box to Use Self-Signed Certs As noted, self-signed certs are typically only recommended for testing
- An option to disable Enforced Domain Name Validation will appear. This option is only available if you have chosen to use self-signed certs
- The final option that is revealed is for the Certificate Chain. This box is only if your trust chain can’t be validated using public trust roots. Copy the certificate chains, separating the Intermediary(s), and Root with a comma
Group Sync
- Group Sync Mappings are only available for Azure Active Directory and Microsoft Graph API Syncs
- Group Sync Mappings will allow you to set up a rule to sync certain groups from Azure to turn on access to an Application within TraitWare as soon as they are part of that Azure group
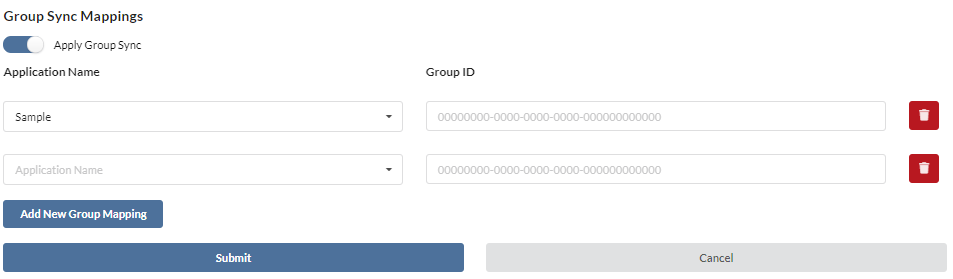
- Select Add Group Mapping to set up a mapping
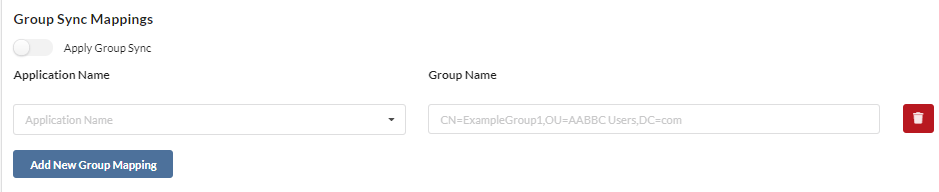
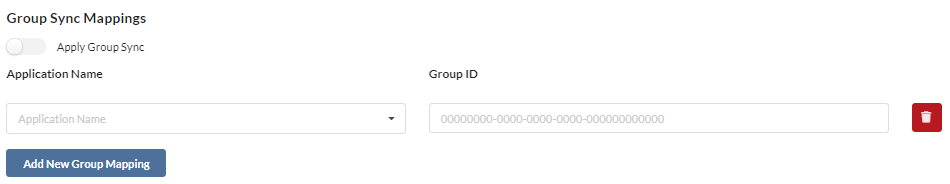
- Depending on which synchronization type you have, your Group Sync Mappings will either require a Group Name or a Group ID
- The Application Name list will populate from whatever applications you have setup with TraitWare
- Choose the Application Name from the dropdown. This will automatically toggle access for the users which are synced from this Group Rule
- For the Group Name, fill out the information which you wish to filter the search results by
- For the Group ID, put the corresponding Object Id from Azure
- Please note that TraitWare does not currently manage user groups. If you wish to create a group to sync to a specific application, create those groups directly in Azure or your AD
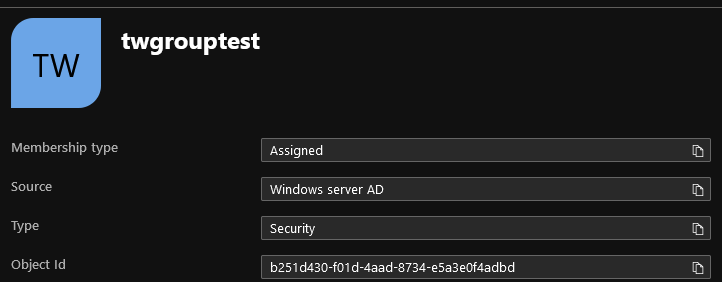
- The sync will not be applied until you have toggled Apply Group Sync
- Each time you select Create New Group Mapping, a new option to add a group will appear
- Once you have added the mappings, select Submit
- You will be able to modify or delete (select the red trash icon) these mappings at any time
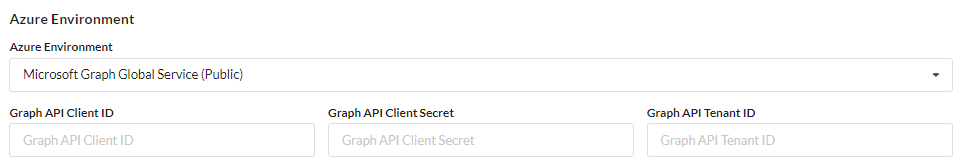
Azure Environment
- If you are syncing to an Azure environment (Azure AD Domain Services or the similar), you will need to complete a GraphAPI to communicate with TraitWare. If you have not received the documentation on how to complete this step, please contact us at support@traitware.com
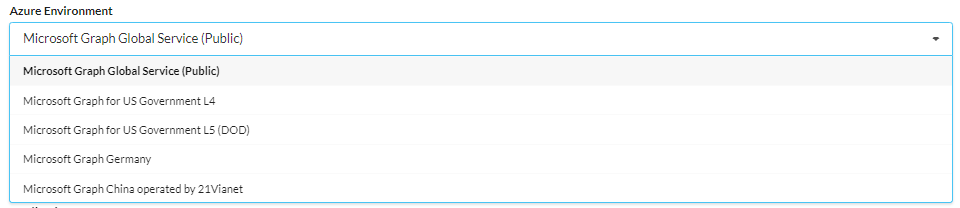
- Under the Azure Environment dropdown, you will find a list of tested Graph Environments. If you do not see your environment on the list, please contact us at support@traitware.com
- Once you have chosen the appropriate environment, you will need to fill out the necessary information which is found in the App registrations on Azure
- As mentioned above, these settings are based on a TraitWare setup and will require specific documentation
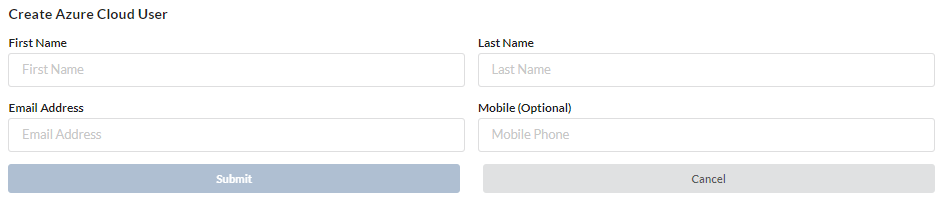
Azure Cloud User
- If you have completed a sync from Azure to TraitWare using LDAPS or a Graph API, you will have the option to create users directly from TraitWare which will be synced to your Azure Cloud
- These users will not be added to any groups but will be immediately ready to access any TraitWare applications once their Azure settings are confirmed
- Make sure that you are using the Verified Federated Azure Domain to create the user’s email
- Once all fields are filled out, select Submit